Is VoIP Safe? — That’s a query a number of IT leaders have been asking currently. And the current compromise on 3CX’s VoIP through a provide chain assault isn’t serving to issues both [*].
For essentially the most half, the character of VoIP entails transmitting voice communications over the web moderately than by means of conventional phone strains.
A sophisticated manner of that is VoIP converts analog voice alerts into digital knowledge packets, that are then transmitted over the web or different packet-switched networks. And the most effective half about VoIP is its price effectiveness, flexibility and integration capabilities.
Nevertheless, the very nature of transmitting voice communications over the web opens up a number of vulnerabilities that may be exploited by cybercriminals.
With this in thoughts, extra questions roll in — how do you safe your VoIP calls? Greatest practices? Mitigation techniques? All of this and extra will probably be answered on this information.
However first —
How Does VoIP Work?
Right here’s a fast run down of how the VoIP system works:
- Voice sign conversion: Whenever you converse right into a VoIP-enabled system (like a smartphone, pc, or VoIP telephone), it converts your voice into digital knowledge. This conversion is completed by your system’s microphone and an analog-to-digital converter (ADC), remodeling the sound waves of your voice into digital packets of information.
- Knowledge compression: Subsequent, it compresses your digital voice knowledge utilizing a codec (coder-decoder).
💡Notice → This step is essential for decreasing the dimensions of the info packets to allow them to be transmitted extra effectively over the Web. Totally different codecs supply a stability between voice high quality and the quantity of information bandwidth used.
- Packetization: The compressed digital knowledge is split into small packets. Every packet is wrapped with a header that accommodates data obligatory for routing and reassembling the packets within the right order as soon as they attain their vacation spot.
- Transmission: The packets are despatched over the Web or some other IP community. To succeed in the vacation spot, they journey by means of numerous routers and networks, which is decided by the routing data in every packet’s header. The Web’s construction permits these packets to take essentially the most environment friendly path accessible on the time of transmission.
- Reassembly: As soon as the info packets arrive at their vacation spot, they’re reassembled into the unique sequence to precisely reproduce the spoken phrases. This reassembly takes into consideration any packets that will have arrived out of order or had been misplaced throughout transmission.
- Decompression and Conversion: The digital knowledge is then decompressed (if obligatory) and transformed again into analog sound waves utilizing a digital-to-analog converter (DAC).
💡Notice → This step is the reverse of what occurred on the sender’s finish.
- Playback: Lastly, the analog sign is shipped to the speaker of the receiving system, permitting the recipient to listen to the sender’s voice as if it had been a standard telephone name.
💡Advisable → How Does VoIP Work? The Newbie’s Information To VoIP Cellphone Techniques
Why VoIP safety issues
Safety is crucial to each enterprise. It doesn’t matter when you’ve got a big group or a small enterprise. A disruption to your telephone system could be nothing in need of catastrophic.
Voice over Web Protocol (VoIP) isn’t any completely different. The decrease prices of VoIP entice a enterprise proprietor. An attacker would love to use your VoIP community whenever you’re not trying.
The excellent news is that VoIP is sort of safe at this time. It has endured even after 20 years of penetration testing. Total, VoIP service suppliers are dependable and safe, whilst the character of safety threats continues to evolve.


JP Morgan surveyed enterprise leaders and found that 94% of corporations had taken steps to harden their infrastructure. Malware, fee fraud, and knowledge breaches topped their worries.
Not like different IT safety threats, Voice over IP presents new alternatives for attackers. Prime dangers embrace name interception, caller ID spoofing, vishing, and Denial of Service (DoS) assaults. We’ll get extra into these specifics later.
VoIP safety isn’t solely about name encryption. It’s in regards to the stage of belief that’s conveyed over a voice and textual content community. Your corporation communication platform can perform extra assaults if it’s compromised.
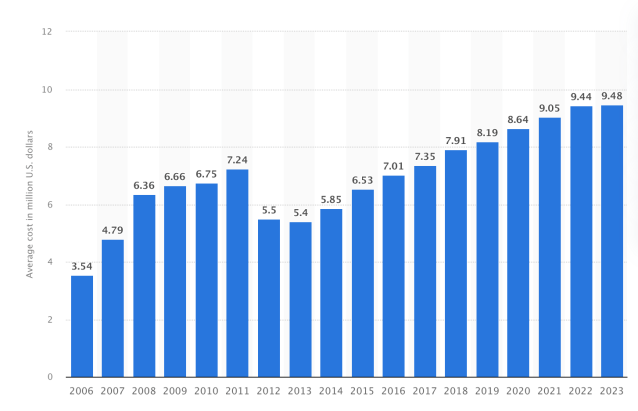
The price of a breach continues to rise yearly. On common, a safety breach in america prices $9.4 million, in response to studies from Statista.

Attackers can perform assaults with the assistance of VoIP, reminiscent of:
- Social engineering through telephone calls.
- Disclosing inside Wi-Fi community passwords.
- Dialing costly telephone numbers (toll fraud).
- Intercepting multi-factor authentication textual content messages.
- Gaining unauthorized entry below the false pretext to knowledge networks.
For instance, Twitter confronted a number of coordinated assaults. The corporate isn’t any stranger to VoIP safety dangers, and former CEO Jack Dorsey was focused in a fraudulent quantity porting request final yr.
This safety concern doubtless had little to do with sturdy passwords. It was worse.
Social engineering may help carry coordinated assaults towards recognized VoIP customers. The Community Operations Middle (NOC) employees and customer support groups are all the time high targets. All it takes is granting unauthorized entry to your organization as soon as, and your intrusion detection system turns into nugatory.
Famed hacker safety marketing consultant Kevin Mitnick compromised programs not solely with technical expertise. He exploited his goal’s willingness to assist. One of the best protection right here is to teach your employees about learn how to spot social engineering.
The excellent news is there are efficient countermeasures to mitigate VoIP safety points. Skilled VoIP networks have develop into proof against abuse from recognized and unknown actors.
Let’s look deeper on the safety threats plaguing enterprise telephone programs.
Associated: How Does VoIP Work? The Newbie’s Information To VoIP Cellphone Techniques
Conventional Cellphone Techniques vs. VoIP


Folks positioned calls over the Public Switched Phone Community (PSTN) for over a century. This voice community is analog. It stays weak wherever bodily entry to wiring is feasible.
This legacy telephone system is also referred to as the Plain Previous Phone System (POTS). Calls are linked utilizing audio alerts, which attackers can intercept with ease.
Within the diagram under, you’ll be able to see that calls cross by means of analog terminals right into a Central Workplace. Cellphone corporations at this time have established safety measures and protocols to make sure safety between Central Workplaces. However that safety doesn’t lengthen to your inside telephone system.
A whole subculture fashioned across the vulnerabilities of enterprise phone programs. Phreaking, a portmanteau of telephone + hacking, is a observe of exploring weak telephone programs. Within the Nineteen Seventies, it was attainable to get free calling over the PSTN. Within the late 90s, phreakers pivoted towards Non-public Department Trade (PBX) tools. That’s, they’ll springboard assaults from insecure company telephone programs. Head to your native Barnes & Noble to select up 2600 and skim in regards to the vulnerabilities of an previous Lucent or Avaya telephone system.
Phone networks at this time separate voice site visitors from the signaling to ascertain calls utilizing SS7 protocol. Regardless of this, many PBX programs stay weak, and attackers will discover them.
Voice over Web Protocol is completely different.


Calls are established utilizing the SIP protocol. Session Initiation Protocol (SIP) acts as a signaling protocol for dependable web telephony. A SIP server compresses voice site visitors into media streams and sends them over an web connection.
It’s clear why massive corporations and small companies flocked to make calls over the web. It saves on IT and communication bills and gives customers with a ton of flexibility to do business from home.
VoIP telephone programs use the identical knowledge community to ascertain telephone calls. The VoIP supplier solely handles all VoIP site visitors. IT employees solely want to take care of a safe community for his or her employees.
Within the diagram under, a secure community connection is required for VoIP telephone service. You don’t must construct or preserve the VoIP infrastructure.
The largest distinction right here is that telephones and identities exist just about. This implies customers can take their VoIP telephones with them and work from wherever. Moreover, it means individuals can use SIP calling apps, also referred to as a softphone, for calling.
VoIP telephone providers supply many safety benefits over conventional telephone programs. Prime advantages embrace:
- Actual-time monitoring of calling plan utilization.
- Strict enforcement of toll-free calls.
- Name encryption to stop eavesdropping.
- Sturdy voicemail options with e-mail supply.
So, what about when VoIP calls attain the PSTN?
Respected VoIP suppliers preserve military-grade safety. They use Session Border Controllers (SBCs) for optimum safety and efficiency. An SBC acts as a firewall that maintains efficiency and logical name routing. Operators preserve excessive requirements to patch for safety vulnerabilities and producer’s firmware updates.
Name logs for an old-school telephone system are sometimes very restricted. This makes monitoring down stolen enterprise knowledge practically unattainable. Extra PSTN dangers fall below gaps in enterprise continuity.
As an example, many PBX telephone programs aren’t nicely supported, alternative components are costly, and discovering certified technicians is difficult. An outage may knock out your corporation communication for weeks.
The underside line is that VoIP telephone programs supply higher privateness, safety, and reliability for companies.
Prime VoIP safety threats
You’re in all probability curious in regards to the sorts of VoIP safety points which might be on the market. Right here’s a rundown of what you’ll must fend towards.
- Denial of Service (DoS) – This assault starves the community of assets to interrupt telephone service and drop telephone calls. This will degrade name high quality, latency, and uptime for a name middle.
- Warfare dialing – The sort of assault entails controlling your PBX to “scan” different phone networks. It really works by dialing numbers to connect with modems or different attention-grabbing extensions.
- Toll fraud – Like conflict dialing, this requires entry to name an out of doors line out of your telephone system. Attackers can dial costly worldwide numbers that rack up costly toll expenses.
- Phishing – This VoIP hack preys on unsuspecting customers who belief their caller ID. Victims disclose particulars in regards to the inside IP community, passwords, or different delicate knowledge.
- Name interception – Attackers use unsecured networks to intercept unencrypted SIP site visitors. To make issues worse, this could embrace video as nicely.
- Spam – It ought to come as no shock the voicemail field is a typical goal for robocalls and different telephone scams. Many use restricted or “Non-public” caller ID.
- Malware – Attackers use completely different malicious software program to telephone or e-mail credentials. This will open up extra alternatives to infiltrate your community and exfiltrate delicate enterprise knowledge.
These threats are most alarming when you’ve arrange a DIY telephone system. As the corporate has expanded, it’s not the precise match. As an example, a self-hosted Asterisk PBX would possibly suffice for some, nevertheless it’s a beautiful goal for hackers. VoIP assaults is perhaps silent and undetected for months.
So, what must you search for in a VoIP service supplier? It’s tempting to look solely at telephone system prices, however there’s extra to think about in the case of safety.
Associated: Healthcare Name Middle Greatest Practices for Higher Affected person Care
Selecting a safe VoIP supplier
The safety of your telephone system comes all the way down to implementation and compliance with safety protocols.
As with every cloud PBX, be sure that the supplier meets safety necessities. These range relying in your business and particular wants. One of the simplest ways to start this investigation is by asking your supplier:
- What accreditations do you will have?
- Do you utilize third-party instruments or software program?
- How do you practice and retrain employees?
- How do you reply to safety incidents?
- Do you supply TLS and SRTP name encryption?
Accreditations
When you’ve answered these questions, dive deeper into your personal VoIP necessities. Listed under are the highest certifications to remember:
- HIPAA Compliance – Well being Insurance coverage Portability and Accountability Act (HIPAA) mandates that healthcare service suppliers safe affected person knowledge. These guidelines additionally apply to their telephone programs, reminiscent of voicemail and name recordings. VoIP servers should be configured to guard affected person privateness.
- ISO/IEC 20071 – This international commonplace establishes that organizations assess and reply to safety threats. It implies that the group has applied rigorous data safety controls.
- PCI Compliance – Cost Card Trade (PCI) compliance mandates that it’s essential to safe your infrastructure when you settle for bank cards. It mandates working system updates and secured VLANs. It additionally requires penetration testing towards your group’s IP addresses. Securing fee knowledge is desk stakes for e-commerce. You danger increased transaction charges and penalties in case your VoIP answer isn’t PCI-compliant.
- SOC 2 Compliance – Service Group Management (SOC) compliance consists of practices to make sure client belief. Not like different requirements, there’s flexibility throughout 5 areas: privateness, safety, availability, and knowledge integrity. Many respected SaaS corporations and cloud-based providers meet SOC 2 compliance.
It’s straightforward to see how these certifications may give you better peace of thoughts. It may be difficult to certify your on-premises PBX or home-grown telephone system working on Amazon or Google Cloud. You don’t wish to take possibilities in the case of VoIP safety.
Ask your VoIP supplier for certifications and evaluate them to your wants. For those who’d like a summarized model of all of the above data, take a look at our fast three-minute video on VoIP safety under:
Associated: A 5-Step VoIP Implementation Information (+The way to Do it Your self)
Buyer communications
One other issue to think about is how nicely the corporate communicates with prospects. How will you inform? Search for its standing web page, which is also referred to as a belief web page. The instance proven under is the Nextiva Standing web page.


Standing pages element updates in regards to the VoIP system and incidents affecting voice service. Are they particular? Are they useful? Are updates timestamped?
Verify if there was any widespread downtime or outages. Search for 99.999% uptime, which means there are solely six minutes of downtime yearly. Moreover, search for deliberate upkeep to use updates to the VoIP community. These typically embrace important working system updates.
The truth of IP telephony is that some interruptions would possibly happen, nevertheless it issues how your VoIP vendor communicates with you about it.
Name encryption
In addition to certifications and simple buyer communication, you need name encryption in 2020. Name encryption makes use of Transport Layer Safety (TLS) and Safe Actual-time Transport Protocol (SRTP). These VoIP protocols work collectively to ascertain high-grade safety in each name.
Unencrypted networks are liable to snooping. In contrast, knowledge that’s encrypted is of no use to anybody who manages to file the info transmission. Encryption that runs from the telephone to the service supplier is essential. Knowledge needs to be encrypted on each attainable layer.
For the best interoperability, SIP isn’t encrypted. Since IP telephony makes use of the IP stack, encryption is managed by the transport layer. When enabled, the VoIP name session and the accompanying name knowledge isn’t accessible to knowledge thieves.
Ask your VoIP supplier about name encryption to make sure your SIP units can use TLS and SRTP.
VoIP safety for healthcare suppliers
If your organization manages affected person knowledge or in any other case must observe HIPAA, maintain studying.
Medical workplaces should shield affected person privateness by configuring their communications programs. This contains your VoIP telephone service. Healthcare suppliers are high targets as a result of affected person data is continuously used to hold out identification theft.
Voice over IP networks meets HIPAA necessities once they put in place correct safety measures. Guarantee your VoIP supplier has agreements with enterprise associates to take care of compliance.
VoIP issues to satisfy HIPAA


Some VoIP customers are unaware that they’re required to disable sure providers to remain compliant. Voicemail transcription, voicemail-to-email attachments, and visible voicemail aren’t allowed.
With Nextiva, you’ll be able to ensure that your VoIP answer is HIPAA-compliant. Tell us, and we will provision your account on our safe VoIP servers.
VoIP safety finest practices
Safety isn’t as obscure as some would possibly suppose. We’ve simplified the most effective practices to make sure optimum safety in your group.
Right here is how one can shield your VoIP community from threats.
- Implement a powerful password coverage. Robust passwords are important to securing your telephone system. Use a mixture of letters, numbers, and non-alphanumerics. Be certain that workers don’t retailer passwords in textual content information or Submit-It notes on their computer systems.
- Apply working system updates typically. Making use of working system updates is a given for many programs directors. Encourage your customers to simply accept OS updates for his or her iPhone or Android. These updates can guard towards malicious software program and exploits.
- Arrange a Digital Non-public Community (VPN) for distant employees. VPNs can encrypt all site visitors no matter the place the worker works. It’s supreme for do business from home employees. Think about a business-grade VPN from Cisco, Sophos, or Cloudflare. Latest tutorial analysis has proven VPNs don’t degrade name high quality.
- Require Wi-Fi encryption. Activate WPA2 in your firm’s wi-fi networks. Instruct workers additionally use this encryption for his or her Wi-Fi community. As a finest observe, replace your Wi-Fi password yearly.
- Evaluate your name logs. Study your organization’s name logs to establish any uncommon calling developments or conduct. Arrange a useful dashboard utilizing a name analytics function to observe name quantity on a weekly and month-to-month foundation.
- Limit your calling and block personal calls. Until your organization does enterprise abroad, you don’t must dial worldwide numbers. Higher but, solely grant entry to worldwide calling to those that name overseas. Verify your VoIP service blocks 1-900 numbers to stop toll fraud. Allow name blocking to display screen restricted/personal calls with a message instructing them to allow their caller ID.
- Deactivate inactive accounts. When workers depart the corporate, don’t neglect to inform your IT employees. By disabling worker accounts promptly, you’ll be able to reduce office disruptions. From a technical standpoint, you don’t need VoIP accounts to stay practical with out a actual person assigned to it.
- Encourage your employees to report unusual conduct. Ask your workforce to report lacking voicemails and ghost calls. A ghost name is when your telephone rings with out a caller. Moreover, advocate they don’t retailer voicemail messages longer than wanted.
- Implement distant system administration. On an enterprise stage, being able to wipe a tool remotely is crucial. Concern laptops with distant administration so you’ll be able to observe and wipe a tool within the occasion of theft or compromise.
- Educate customers on safety practices. Remind customers that you just received’t ever want their password. Practice them to identify phishing and social engineering scams. Conduct common safety assessments to find rising vulnerabilities. Final however not least, be sure that they know who to contact within the occasion of a safety breach.
Whereas numerous these finest practices overlap with community safety, take a look at them by means of the lens of an attacker.
Executives rely upon you to maintain them protected from the ever-changing safety panorama. By following these, you’ll reduce the impression of a safety incident.
The way forward for securing telephone programs
VoIP has matured from a private service to an important enterprise communications platform.
The grass is all the time greener the place you water it. VoIP has been put by means of its paces to show worthwhile for organizations. Safe SIP-based calling is now the usual.
Sustaining an on-premises PBX and different telephony tools is an enormous duty. The telephone system isn’t any completely different as organizations offload their e-mail programs and webhosting to the cloud.
A cloud telephone system like Nextiva permits IT employees to sort out greater initiatives. As an alternative of tinkering with previous tools, they’ll equip the corporate with a distant workforce.
Closing ideas on VoIP safety


Organizations that safe voice site visitors are extra resilient than people who sit idle. If there’s something 2020 taught us, it’s that you just should be ready for each contingency.
Based on findings from the 2020 U.S. CEO survey from PwC, 53% of CEOs had been “extraordinarily involved” about cybersecurity. That is astounding, provided that cyber threats outweighed coverage, commerce, authorities regulation, and geopolitical uncertainty.
A lot of the safety duty rests with sustaining operational safety. You’ll be able to higher mitigate threats by accepting VoIP telephones as highly effective community home equipment.
Regardless of all this, safe VoIP suppliers can solely accomplish that a lot. You could fortify your inside community defenses and educate customers first.
A good enterprise telephone service could be the reassurance that you must preserve a safe calling atmosphere. Test their certifications and analysis their reliability, safety measures, and name encryption capabilities.
The Cellphone System IT Loves
Enterprise safety. Uncompromising options. See Why IT Groups Belief Nextiva for Their Firm’s Cellphone Service.
