Half I
Typically Ethereum is in comparison with a singleton Digital Machine. Whereas that is appropriate in some sense; I believe it is a little more. To start with what’s a singleton in a distributed system? It’s merely a set of values that some threshold of contributors have come to consensus on. A Digital Machine is a computational atmosphere that’s remoted from the bodily laptop and from different environments.
A hypervisor permits the bodily machine to be multiplexed into many VMs. In response to this definition a typical hypervisor is the net browser the place webpages are VMs. One other instance of a hypervisor can be Ethereum as every contract will get its personal remoted computational atmosphere.
There are numerous variations between the frequent net browser and Ethereum, however one of many extra fascinating ones is how VMs talk and work together with one another. Internet browsers don’t present a method for VMs to instantly work together whereas Ethereum alternatively gives some easy mechanism for VM interplay; the opcodes CALL, DELEGATECALL, CALLCODE, CREATE. On this submit will discover the query; What different guidelines may exist? Can we generalize VM interactions and supplied an summary framework for these interactions? And from this framework can we purpose about distributed hypervisors?
Most of this submit will resemble ambient calculus however there are a number of notable variations from ambient calculus and what’s offered right here. The diagrams could be considered bigraphs however they need to even be self explanatory. Half I’ll describe the foundations of ambients after which apply them to Ethereum. Half II will focus on scaling within the phrases of ambients as laid out by half I.
What’s an Ambient?
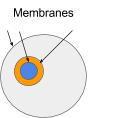
An ambient is a bounded place through which computation can happen. A boundary determines what’s inside and what’s outdoors an ambient. For ambients we name this boundary a membrane. The world inside an ambient is hierarchical namespace. Objects can exist inside an ambient. The objects are addressable through the namespace. There are three base components in ambient calculus. Objects, Namespaces and Messages.
Hierarchical Namespaces
One of the crucial acquainted namespace is the file system tree. Namespaces enable us to establish objects with paths or names. Namespaces right here have the next properties
- For each doable path there exists a null or an object
- At any level within the namespace you’ll be able to transfer up or down. That is what’s implied by hierarchical.
- Each path has a root related to it. The foundation uniquely identifies the content material for all of the paths beneath the foundation. You possibly can consider the foundation as a pointer to the content material of the trail.
- Paths could be learn from or written to
- Messages could be despatched alongside paths to things
Object Sorts
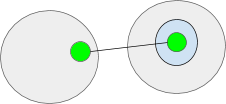
What’s an object? It’s only a worth. In actual life computing its just a few knowledge. This knowledge could be interpreted in a number of other ways. Any Object could be learn as knowledge. The pink circle is a few knowledge that exists within the gray ambient.
Objects can be interpreted as ambients. This permits ambients to have sub-ambients. Right here the orange and gray circles are ambients.
Objects can be interpreted as ports. Two or extra ports type a I/O channel. Channels enable messages to be despatched to ambients in a unique namespaces. Channels could be considered tunnels by means of an ambient’s membrane. Each the doorway and exit ports should exist someplace in a namespace. Right here the inexperienced objects signify ports.
Lastly messages can be thought of to be an object. Messages are particular since they’re outlined as objects in movement or considered objects with velocity.
To Recap; Objects could be the next varieties
Objects :: =
Information
Port
Ambient
Message
Messages
As acknowledged above messages are objects which can be in transit. Messages could be despatched by means of a namespace and thru channels. Messages have the next properties which can be set by the programs message handler. They don’t seem to be all intrinsically a part of the message however as you will note later they make working with messages simpler.
- To – The trail to the vacation spot of the message. That is immutable.
- From – The sender of the message. That is immutable.
- Sort – The kind of message. That is immutable.
- Information – The message’s physique. That is immutable.
- Heading – The vacation spot relative to its present place. If `Heading` is `null` then the message has arrived at its vacation spot and can journey no additional. This isn’t instantly encoded within the message however as a substitute set by the programs message handler. That is mutable.
- Course – Which route the message is touring. It will possibly both be going ‘out’ of the ambient or going ‘in’ to the ambient. That is mutable.
Message Sorts
Message have the next varieties which have corresponding instructions used to ship them.
Set(path, worth) - Units a path to a given worth
Get(path) - Will get a worth of the given path
SetRoot(path, root) - units the foundation of `path` to `root`
GetRoot(path) - Will get the trail’s root
Name(path, knowledge) - Sends a message alongside the given path
Join(to, from, choices) - creates a channel between two paths.
Deleting
It may not be instantly apparent methods to delete an ambient or different objects. To do that we use the `Set` and `SetRoot` message.
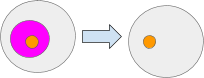
The Set message units the worth of a path. Setting a path to null is equal to deleting the contents of that path. For instance Set(‘pinkAmbient’, null) Right here the pink ambient is about to null. Be aware the the orange ambient was not deleted.
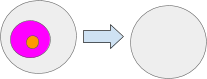
The SetRoot message units the foundation of a path. If the foundation is about to null all the trail values beneath the foundation will turn into null. For instance CopyRoot(‘pinkAmbient’, null) will set the pink ambient’s root to null which may even trigger the orange ambient be to null.
In fact if we did one thing like SetRoot(‘a’, ‘pinkAmbientsRoot’) we might copy the pink Ambient and all of it contents to path “a”
Iterating the by means of a Namespace.
In lots of instances it helpful to iterate by means of all of the ambients in a given namespace. A technique we may method that is to `get` every path within the namespace. However the issue is that almost all namespaces are infinite. A greater method can be to offer an express iteration technique. Let’s add a message
Subsequent(path) - Given a path return the subsequent non-null path within the namespace.
This means that namespaces all will need to have an order. Additionally this gives us with a pleasant strategy to construct extra difficult ambient operations like merging two or extra ambients. We additionally want this to construct kind checking.
Membrane computing
The ambient’s border is its membrane. It will possibly filter message coming into and going out of it. For instance the if the gray ambient sends a Set(‘blueAmbient’, null) message to the trail of the ‘blueAmbient’ it should undergo the membrane of the orange ambient. The orange ambient can determined whether or not or to not let the message go by means of.
A Membrane API
Lets stroll by means of a small instance of what programming ambients may appear to be.
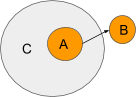
Ambient A is attempting ship a message to ambient B however the message has to undergo Ambient C. Since A is a sub-ambient of C, C can management this message. Here’s what an api for coping with messages may appear to be. Let say that now we have a operate ‘onMessage’ that will get ran at any time when the ambient will get a message. Here’s what C membrane may appear to be.
/** * Permit any message to go by means of the membrane besides messages from Ambient D * @technique onMessage * @param message - the message that's leaving the ambient * @retruns Boolean */
operate onMessage(message) {
if(Message.sender != ”A” && Message.route == ‘out’){
Message.heading = ‘D’
}
}
C filters any messages coming from the trail ‘A’ which can be going out of it. As a substitute of letting the message go to its supposed location C reroutes the message to location “D”. Discover how C set the heading on the message. If C set Message.heading to null then the message would cease there. C can solely determine the place to ahead the message or to cease it.
The flexibility of ambients to filter and determine which message can journey by means of them is a crucial one. That is often known as Membrane computing. It would permit you to construct versatile and simply composable contracts. Particularly relating to administration of sub-contracts.
Mapping ambients to a Ethereum
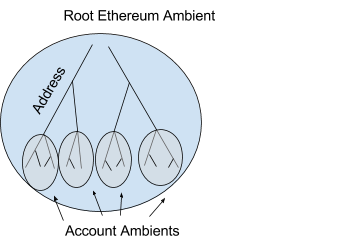
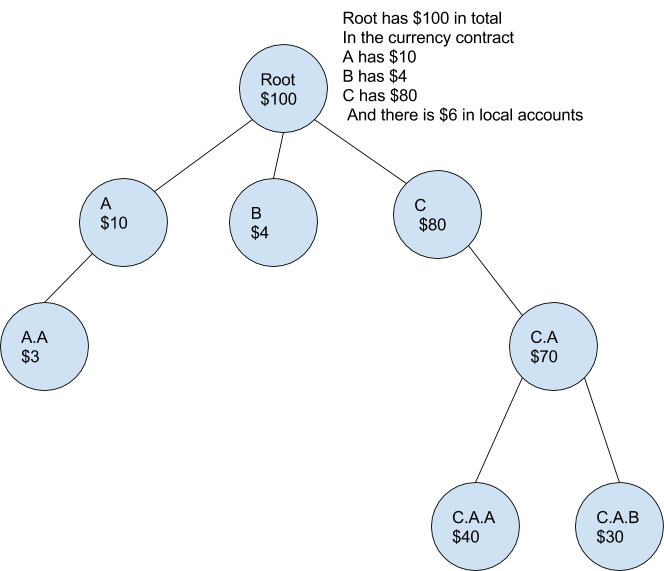
Now that now we have the fundamentals of ambients let’s apply them to a one among our favourite knowledge constructions, the merkle tree. To begin you may need already acknowledged the truth that a contract in Ethereum is like an ambient and the namespace is supplied by the merkle tree.
Namespace ::=the merkle tree
This may very well be visualized like this
In Ethereum every ambient has an deal with that’s 20 bytes lengthy and appears like the next 0x1158c3c9a70e85d8358972810ed984c8e6ffcf0f. Ethereum ambients have storage that enable them retailer retailer arbitrary values completely. Storage is accessed and manipulated with the SSTORE and SLOAD opcodes. The equal to those are the set and get messages. Additionally command Name is equal.
SetRoot, GetRoot and Join should not have equivalents in Ethereum presently. SetRoot and GetRoot would learn from and manipulate the underlying mekle trie.
Now we’re going to deviate from present Ethereum to Ethereum + Ambients. Allow us to say the contract 0x1158c3c9a70e85d8358972810ed984c8e6ffcf0f units the worth ‘doge’ on the addresses ‘coin’ which is 636f696e in hex. The deal with 0x1158c3c9a70e85d8358972810ed984c8e6ffcf0f/636f696e would then comprise the worth ‘doge’. Additionally ‘doge’ may be interpreted as code if a Name was made to that path.
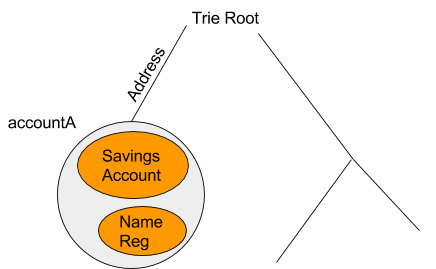
Private Accounts
Lets use a private Ethereum account for instance. For comfort we’re going to say the deal with of the account is “accountA” which can be represented because the gray ambient. This ambient would maintain the fundamental signature validation code as seen within the foreign money and crypto abstraction. If the consumer wished to put a spending limits on herself then she may create a “Financial savings Account” which might solely allow a specific amount of ether to be spent per day. Moreover the consumer may create her personal customized Identify Reg or different monetary apps. The hierarchical nature of the ambients means that you can construct up administrative “zone”. They will make code very modular for the reason that “saving account” and different contracts don’t have to have any code devoted to checking if the consumer is an admin or checking different credential since that may very well be executed by the accountA’s ambient.
On this part we are going to discover some concepts about scalability by way of ambients.
The essential concept of scalability is pretty easy. Most strategies proposed to this point contain these properties:
- Separating some a part of the state right into a shard that’s processed unbiased of the opposite shards
- Some type of cross validation; the place some portion of a shard’s work is checked by different shards which is often triggered by cross shard communication.
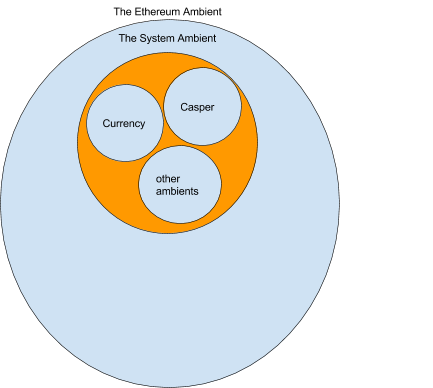
We’re additionally assuming now we have a Proof of Stake algorithm like Casper and this algorithm is carried out in a set of ambients. Together with casper now we have a foreign money ambient that tracks the quantity of ether every account ambient has. These ambients are grouped collectively into the system ambient. There perhaps many extra ambients within the system ambient however for now we are going to simply contemplate these.
For now we are going to merely assume that casper works and produces the proper state for the “Ethereum Ambient”.
Sharding
If Ethereum is profitable, the quantity of transaction will improve over time. After some time a excessive quantity of transactions will trigger the value of gasoline to extend. At a sure threshold decided by a Threshold operate the Casper ambient will produce a shard. It must be famous that solely from the casper ambient’s perspective is Ethereum sharded. Everybody else sees Ethereum as one continued namespace extending by means of many ambients.
There’s some threshold that’s wanted to create a shard in Casper. This isn’t the main focus of this submit however we are able to picture a number of the parameters it may be primarily based off of. It may use gasPrice to transaction ratio. Or may it use a voting system or a bidding system or mixture of all them.
Apart from the Threshold operate we are going to assume the next about Casper:
- Anybody can contest a state transition.
- Validators are randomly assigned to shards. These type a validation group that run Casper for that shard.
- Validator could also be assigned to a couple of shard
- New shards should be initially validated by all validators
- The overall quantity in bond in a validation group of a shard must be equal to what the shard is value.
Creation of Shards
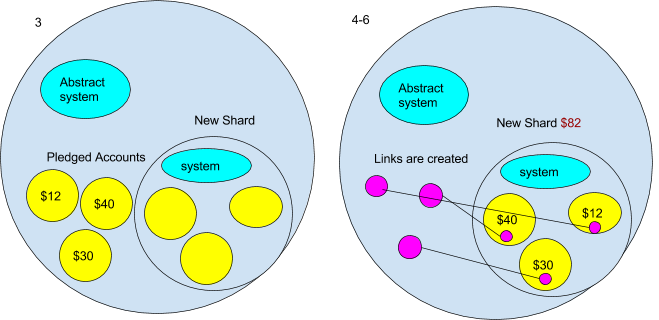
- For now we are going to assume that new shards will begin out as an empty ambient. However take note this may not all the time be the case- for instance a very efficiently dapp may maybe pay the Casper contract sufficient to make it worthwhile for the validator to create a shard out of it. However for now it’s empty.
- The very first thing that occurs to the brand new shard ambient is the system contracts are copied to it. However we don’t need a precise copy of the present system ambient. It is because it incorporates the present state. We wish an empty foreign money contract and an empty Casper contract, and many others. To do that the Ethereum ambient will need to have an “summary” system ambient from which we then copy. We will picture the summary system ambient would have a message handler that solely allowed messages that have been copying it. It may appears to be like one thing like this:
operate onMessage(message) { // disallows messages getting any subambient // roots from the summary system if(message.kind !== `getRoot ` || message.headed !== ‘’){ message = null // kills the message } }The brand new shard would ship a `getRoot` to the summary system. Then it will use `setRoot` internally to repeat the summary system its namespace.
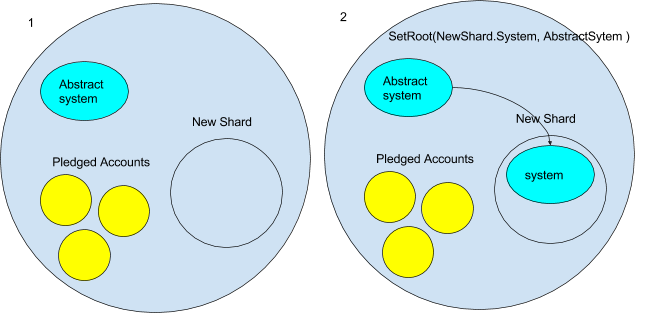
- A part of the brink operate may be pledges from different ambients to maneuver to a brand new shard as soon as it’s created. When the brand new shard is created, all of the accounts that pledged to maneuver are mechanically moved to the brand new shard. That is executed after the system ambient is in place. The accounts are additionally copied with the `CopyRoot` command.
- After they’ve been copied their authentic deal with is changed by a port (created by the “Join” command) making a channel to their new account on the brand new shard.
- The foreign money contract then units the quantity of ether that the shard has to the sum of the accounts that pledge to maneuver.
- Lastly the within the new shards foreign money, the contract is populated by the values of the copied accounts.
Fractal chains?
The tip consequence can be that the highest stage ambients not “see” the person accounts which can be within the new shard, as a substitute it solely see the worth of the sum of the account on the brand new shard ($82 within the diagram). Whereas the brand new shard’s foreign money contract retains observe of the person accounts within the shard. This resembles a fractal in the best way that a part of the entire is encoded in each part of the construction.
Additionally if anybody makes use of the outdated deal with of an ambient that moved, their messages can be forwarded to them through the channels. There are some disadvantages to utilizing the channels; 1) its can be extra pricey 2) there can be larger latency.
Monetary Isolation – Counterfeiting Assaults
The shards could be seen forming a hierarchy; every shard ambient preserving observe of its accounts and the sum of the accounts in its youngsters shards.
This creates a powerful assure of the correctness of account balances. No shard can create counterfeit foreign money and ship it to a different shard. Moreover the safety is additive. That means that the extra shards {that a} message crosses the stronger the assure that it’s appropriate. We’re assuming that each validation group will test that transaction going by means of it. If a transaction goes from shard C to C.A.B then shards C, C.A and C.A.B all will test the transaction and ask the shard C for merkle proof of the sender’s account. If the transaction was discovered to be invalid after the validator’s accepted it then the validators in all three teams would lose their deposits. If accounts have been defrauded they might first be refunded from the validators deposits.
Let’s contemplate a protracted vary counterfeit assault. That is the place a validation group on a shard creates an account with an invalid quantity of foreign money related to it after which they only go away it within the shard. In the event that they ever attempt to transfer it from the shard the mother or father validation group will request an entire transaction log that reveals how the accounts obtained its cash. At this level the assault would fail until the mother or father validation group was additionally compromised. And in a protracted vary assault the attackers wait till the mother or father validation group is compromised. The easiest way to counter that is to make every validation group answerable for the entire historical past of its shard and to not launch the bonds to unbonded validators after a number of epochs. This offers the present validation group an incentive to test the earlier validation teams work.
A technique through which a validation group can test the earlier validation group work rapidly is to simply sum the transaction graph. We will consider all messages that switch foreign money as forming a directed graph. Since we all know the worldwide quantity of foreign money that the shard has, a validation group simply must sum up the entire quantity the accounts had for every block within the earlier epoch and test it in opposition to the recognized world quantity.
To recap, a number of properties that may improve safety are:
- Give the Mum or dad Validation group an incentive to test the work of their youngsters.
- Give validator an incentive to test earlier work
Validation Group Teams (Hierarchical validation teams)
Validators could should put up a really excessive bond to take part in validation. The quantity of bond wanted is a operate of the goal variety of validators which is a operate of the variety of shards that exists.
However this poses an issue since if there have been a better variety of validators it will be more durable to coordinate a bribe assault on a shard however alternatively Casper can turn into inefficient when there are giant variety of validators. A technique this may be solved is to have validators themselves composed of validation teams. The validation group would run in a separate ambient on a separate blockchain from Ethereum.
Within the validation group ambient, work is additional subdivided into smaller chunks. Every particular person validator would get assigned a number of ambients from the shard that validator group was assigned to. This could successfully enable even a small system to take part in validation rising the entire variety of contributors that briber must doubtlessly coordinate with.
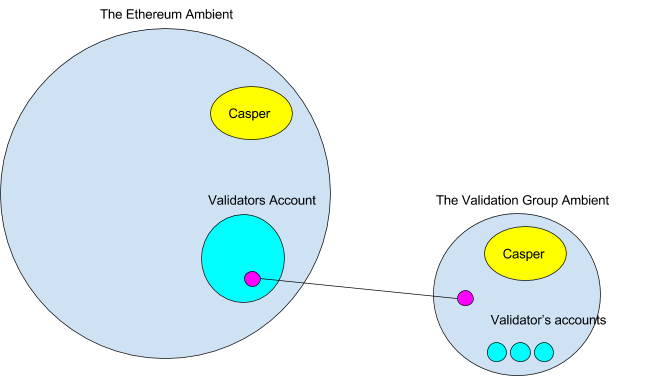
Channels outdoors the Ethereum ambient
To do that the validation group would create a brand new ambient that was related by a channel to the validator group’s ambient. You may surprise how it’s doable to hyperlink to an ambient outdoors of Ethereum. However beneath its easy.
Initially there would solely be a validators account managed by multisig on the Ethereum blockchain. Then the validators would create their very own blockchain (represented as an ambient) which might have the identical system ambients and Casper ambients as Ethereum. After creation, the validator group would join the 2 ambients with a channel. Any message coming into or exiting the ports the should be agreed upon by all of the validators, so the channel must also be protected by a multisig. The code for the multisig would exist within the ports message handler. The channel may solely be adopted by these operating each units of ambients. Nodes operating simply the Ethereum ambient would see the channel however wouldn’t be capable to observe it.
This gives a sample that may very well be elsewhere because it gives a generic strategy to join arbitrary ambients to the Ethereum blockchain. These ambients may stand for the state of your private laptop or an arbitrary feed of information. Past the examples given right here, there are a lot of different design patterns that make pondering in ambients helpful. Whereas there are nonetheless many lacunae ambients may very well be a helpful mannequin for computational environments. Ambients provides a brand new dimension to Ethereum’s hypervisor. Fairly actually too. It permits for contract to be much more modular and gives for a handy strategy to create administrative domains and mannequin many on a regular basis conditions.
NOTES and PROBLEMS
Listed here are some further issues to consider.
- SetRoot must fail if the foundation didn’t exist within the present namespace. If SetRoot was explicitly used the mother or father namespace (../<root>) then that tree can be copied to the namespace. If this occurred between shards the tree can be serialized right into a transaction.
- Message
- All messages are assumed to be async. messages can timeout.
- Messages all have a response. The response should be recoded as transaction on requesting shard and the responding shard.
- Blocks would want two elements; in transaction and out transactions.
- Seize and delete – The sibling ambient units a worth to a path above one other sibling with code for to create an ambient that deletes all of its sub-ambients.
- Answer 1 any motion that may have an effect on a sibling ambient should undergo its message handler
- Answer 2 an ambient may outline a message deal with for all inner message that explicitly disallowed sure varieties of messages.
- Answer 3 reintroduce capabilities as offered in ambient calculus