If there’s one factor working cross-functionally has taught me, it’s that safe entry isn’t only a safety precedence; it’s a progress enabler. Sluggish logins and brittle VPNs kill momentum; over-permissive entry invitations incidents.
The distinction typically comes all the way down to the platform behind the scenes. The strongest zero belief networking software program don’t simply gate entry, they align id, gadget posture, and app context so customers get the place they should go, rapidly and safely.
To see what really stands out, I in contrast main ZTNA options throughout coverage depth, IdP/EDR integrations, deployment pace, and day-two operations.
In the event you’re trying to find one of the best zero belief networking software program for 2025, listed here are my prime picks. Whether or not you’re standardizing on a single consumer or segmenting delicate apps first, these platforms stood out for flexibility, scalability, and real-world usability.
5 finest zero belief networking software program for 2025: My prime picks
- Palo Alto Networks IoT/OT Safety: Greatest for enterprise IoT/OT visibility and management
For auto-discovering related units, assessing danger by conduct, and imposing segmentation to dam lateral motion. - Okta: Greatest for identity-driven entry throughout blended stacks
For safe SSO/MFA, fine-grained conditional entry, and seamless integration with cloud and on-prem apps. - Zscaler Non-public Entry: Greatest for zero-trust entry to inner apps (no VPN)
For brokered user-to-app connectivity, steady id/gadget checks, and quick international entry from anyplace. - ThreatLocker: Greatest for endpoint least-privilege and allowlisting
For default-deny utility management, granular elevation approvals, and ransomware-resilient endpoint insurance policies. - Cato SASE Cloud: Greatest for unified community + safety at international scale
For converging SD-WAN and SSE, imposing zero-trust insurance policies from the cloud, and delivering constant efficiency worldwide.
These finest zero belief networking software program are top-rated of their class, in accordance with the newest G2 Grid Reviews. Contact the gross sales group for correct pricing particulars.
5 finest zero belief community safety instruments I like to recommend
Zero belief networking platforms implement “by no means belief, all the time confirm” for utility entry throughout hybrid and distant work. As an alternative of routing customers by way of network-level VPNs, they repeatedly validate id, gadget posture, and context, then grant exact, app-level entry that limits lateral motion.
The enterprise case is easy: breaches are expensive and customary. IBM states the worldwide common price of a knowledge breach is about $4.4 million, reflecting a 9% drop from the earlier yr, a decline largely attributed to organizations detecting and containing incidents extra rapidly..
With that in thoughts, I prioritized platforms that pair clear coverage fashions and robust integrations (IdP/EDR/MDM) with dependable purchasers and clear visibility. Primarily based on critiques, demos, and hands-on checks, these are the 5 I’d decide in case you’re critical about operationalizing zero belief.
How did I discover and consider one of the best zero belief networking instruments?
I began with G2’s Grid Report, which ranks instruments primarily based on actual person critiques and market presence, to maneuver previous surface-level comparisons. The Grid gave me a strong basis that highlighted each established leaders and revolutionary challengers within the zero belief networking class.
I then used AI-assisted evaluation to dig into lots of of verified G2 critiques. I paid shut consideration to patterns round coverage reliability and enforcement, ease of integration with id suppliers (IdPs), EDR/MDM, and SIEM instruments, depth of gadget posture checks and app discovery, and scalability throughout customers, apps, and areas. This helped me see what safety, IT, and networking groups truly worth most — and the place zero belief platforms generally fall quick.
To carry the information into real-world context, I additionally related with fellow G2’ers who work with zero belief entry in safety operations, IT, and community engineering. Their experiences validated the themes I discovered within the critiques and make clear implementation pace, setup expertise, and the day-to-day influence these platforms have on each person productiveness and general safety posture.
All product screenshots featured on this article come from official vendor G2 pages and publicly accessible supplies.
What makes zero belief networking software program value it: My opinion
I thought of the next components when evaluating one of the best zero belief networking software program.
- Coverage accuracy and enforcement: One of the best platforms transcend broad community guidelines, imposing least-privilege on the app stage with steady checks on person, gadget, and context — and dealing with advanced eventualities with out breaking workflows.
- Protection throughout non-public apps and SaaS: Robust platforms safe east–west and user-to-app visitors alike, supporting legacy/non-public apps, fashionable SaaS, and even contractor/BYOD entry with constant controls.
- Id, gadget, and safety stack integrations: I prioritized instruments that plug cleanly into IdPs, EDR/MDM, SIEM, and DNS/safe internet gateways to maintain insurance policies and telemetry unified. Particularly essential for enterprise patrons, I thought of platforms that assist robust encryption, knowledge residency choices, and attestations like SOC 2/ISO 27001 to guard delicate knowledge.
- Segmentation and lateral-movement protection: Options that may uncover apps, visualize flows, and implement microsegmentation stand out for holding incidents and lowering blast radius.
- Scalability and suppleness: One of the best instruments serve lean IT groups and enormous enterprises, providing wise defaults, API/extensibility for superior use instances, and a world footprint that holds up underneath load.
The checklist under incorporates real person critiques from the Zero Belief Networking class. To be included on this class, an answer should:
- Make the most of adaptive authentication to repeatedly confirm person permissions
- Permit for community segmentation to simplify and broaden coverage enforcement
- Monitor visitors and person conduct for future inspection and evaluation
*This knowledge was pulled from G2 in 2025. Some critiques could have been edited for readability.
1. Palo Alto Networks IoT/OT Safety: Greatest for enterprise IoT/OT visibility and management
Amongst platforms constructed to safe blended IT/OT environments, Palo Alto Networks IoT/OT Safety repeatedly exhibits up in G2 critiques for doing the unglamorous work properly: discovering and classifying units, surfacing behavioral anomalies, and giving groups a unified, searchable view of what’s truly related.
In case your aim is to maneuver from guesswork to a defensible, real-time asset image, that is the sort of basis you want.
What stood out in my analysis (and echoed by G2 customers) is the unified IT/OT lens. Reviewers constantly spotlight how the product brings operational know-how into the identical line of sight as conventional IT, making it simpler to see PLCs, HMIs, cameras, sensors, printers, with out stitching collectively a number of instruments. That consolidated view isn’t simply beauty; G2 customers say it shortens triage as a result of possession is clearer and suspicious conduct is simpler to identify in context.
Discovery and classification accuracy additionally got here by way of strongly in G2 critiques. Dependable fingerprinting of IoT/OT belongings and quicker stock buildouts translate to fewer blind spots, faster identification of unknowns, and extra confidence if you connect coverage. Paired with behavioral and anomaly detection, groups report actionable alerts that enhance with tuning — much less noise, extra sign — so responders aren’t sifting by way of countless low-value occasions.
Integration depth is one other repeated theme in G2 suggestions. The product performs properly with id (IdP), endpoint (EDR/MDM), SIEM, ticketing, and NGFW/Prisma workflows. That issues if you need detection to result in enforcement or if you want incidents to indicate up the place your group already lives; reviewers often point out how these connections scale back swivel-chairing, tighten response loops, and make audit narratives clearer.
G2 customers additionally name out dashboards and reporting. Topology views, danger summaries, and device-level drill-downs make advanced environments legible and defensible: you possibly can present what’s speaking to what, why it’s dangerous, and what actions you took. For a lot of groups, that “present your work” second is what turns a very good pilot into an operational win.
G2 reviewers just like the depth and unified view, however a number of observe the console can really feel dense at first, particularly in multi-site rollouts the place roles, teams, and workflows want planning. That stated, the identical G2 suggestions factors to a fast settlement as soon as onboarding is completed: alert noise drops, possession is clearer, and investigations transfer quicker as OT alerts feed present SIEM/SOAR pipelines.
As a result of it consolidates significant capabilities, some G2 customers describe pricing and licensing as being on the upper facet and say they’d like clearer guardrails as gadget counts develop. Nevertheless, groups that plan for future scale and forecast utilization early on report that prices develop into simpler to foretell and that consolidation in the end offsets spend by lowering assist tickets, closing visibility gaps, and strengthening audit readiness.
General, rated a 4.3/5 on G2, reviewers admire that it might probably introduce it alongside present community and safety architectures after which elevate controls as visibility improves. It’s a sensible path to lowering danger with out pausing the enterprise. Repeated G2 themes level to a platform that delivers a reliable stock, fewer blind spots, and quicker, better-informed selections when one thing begins behaving out of band.
What I like about Palo Alto Networks IoT/OT Safety:
- The unified IT/OT lens makes inventories and investigations really feel sane. I can see PLCs, HMIs, cameras, and endpoints in a single place, which strains up with what G2 customers repeatedly name out about quicker, clearer triage.
- Discovery/classification plus significant anomaly detection provides me actionable alerts; sign improves with tuning, and integrations (IdP/EDR/SIEM/NGFW) push these insights into the instruments my group already makes use of.
What G2 customers like about Palo Alto Networks IoT/OT Safety:
“We make the most of Palo Alto Networks OT Safety (GlobalProtect) to permit us to work remotely. This was particularly required throughout the COVID-19 pandemic. As well as, it allowed us to work at numerous areas across the earth, since there have been a number of gateways. I like how there have been a number of methods to signal into Palo Alto Networks’ International Shield. For instance, we had been capable of check in by way of International Shield by way of (Worker Key Card, password/username, MFA {hardware}). That is simple to make the most of on a regular basis, since Staff must signal into our enterprise community to be able to entry Firm paperwork, code, and so on. We principally wanted this each day whereas working remotely.”
– Palo Alto Networks IoT/OT Safety assessment, Verified Person in Protection & House.
What I dislike about Palo Alto Networks IoT/OT Safety:
- The console favors depth and management, which fits groups that need granular coverage and wealthy telemetry, however it might probably really feel dense at first for teams anticipating a plug-and-play setup.
- Enterprise-grade protection and integrations scale properly, although pricing/licensing can require upfront modeling as environments develop. Groups in search of easy per-device predictability might want clearer price guardrails.
What G2 customers dislike about Palo Alto Networks IoT/OT Safety:
“I want the licensing had been extra easy—each further sensor appears to nudge the invoice up. The UI slows down after I pull a month of logs, and some OT-specific signatures nonetheless hearth noisy alerts that we’ve to tune out. Reporting exports are restricted to CSV, so constructing Grafana dashboards means further ETL work on our facet.”
– Palo Alto Networks IoT/OT Safety assessment, Ramon F.
Discover one of the best Community Entry Management software program on G2. Examine prime NAC instruments constructed to implement zero belief insurance policies and safe each gadget in your community.
2. Okta: Greatest for identity-driven entry throughout blended stacks
Amongst id platforms powering zero belief entry, Okta exhibits up repeatedly in G2 critiques for making day-to-day sign-in less complicated whereas tightening management behind the scenes. It’s constructed for groups that need clear SSO, reliable MFA, and broad app integrations with out forcing customers by way of a maze of one-off credentials.
In case your aim is to centralize id and make entry selections primarily based on person, gadget, and context, throughout cloud and on-prem, this can be a robust anchor.
It delivers on core outcomes G2 customers care about: friction-light single sign-on that cuts password sprawl; dependable authentication (from OTP and push to phishing-resistant strategies) that doesn’t lavatory down on a regular basis workflows; and deep integrations with a large ecosystem of SaaS and legacy apps so that you’re not constructing brittle, one-off connectors. In truth, 93% of G2 customers price the authentication expertise extremely.
Reviewers constantly spotlight how rapidly customers adapt to the Okta dashboard/portal, launching the apps they want with out searching hyperlinks, and the way admins can plug Okta into the remainder of the stack (HRIS for automated onboarding/offboarding, EDR/MDM for gadget posture, SIEM/ticketing for visibility and handoffs). That ecosystem match exhibits up within the suggestions as fewer “the place do I log in?” tickets and smoother day-two operations.
From an operator lens, G2 reviewers repeatedly name out usability. The setup feels easy, insurance policies are comprehensible, and on a regular basis administration doesn’t require deep id engineering. 94% of G2 customers price its self-service password reset characteristic extremely.
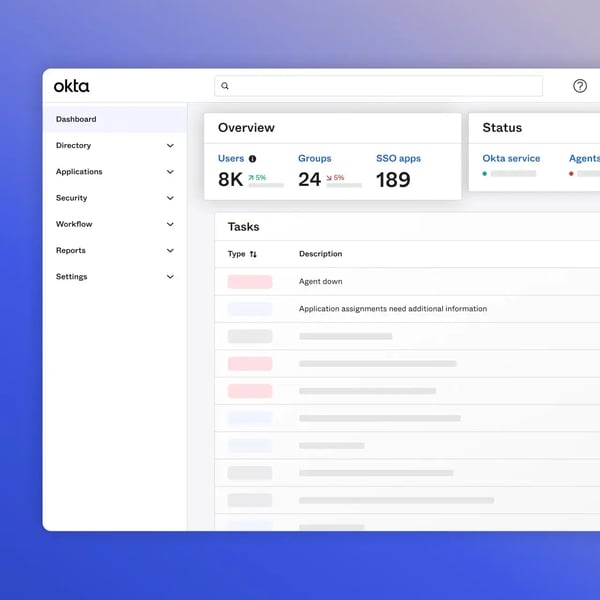
Groups like that app project and group-based insurance policies scale cleanly because the org grows, and that availability/efficiency is strong sufficient that sign-in fades into the background for many customers. When the platform is wired into your present instruments, audits get simpler as a result of entry paths are centralized and logged.
Safety depth past SSO. Reviewers often spotlight Okta’s robust coverage engine and adaptive entry controls, together with context-aware selections primarily based on gadget, community, and danger alerts, which strengthen zero belief posture with out including complexity. Intensive integration ecosystem. A number of critiques reward Okta’s broad connector library and prebuilt app integrations, which scale back customized improvement work and make it simpler to plug id into the broader safety stack.
Customers additionally say that Okta is dependable and extremely accessible. A number of customers level to constant uptime and robust efficiency, noting that authentication stays steady whilst visitors scales or throughout peak utilization durations.
Let’s speak about console density. G2 reviewers worth the management and breadth, fine-grained coverage and broad integrations, whereas noting the console can really feel busy in case you’re anticipating plug-and-play. That density fits admins who prioritize high-signal telemetry and exact coverage design; groups in search of a light-weight, minimalist UI could discover it greater than they want.
G2 reviewers additionally speak about stricter entry posture. Robust insurance policies and gadget checks increase assurance on delicate entry, and G2 customers observe this will floor extra prompts than “invisible” setups. That’s a win for organizations that favor risk-tight enforcement; in case your bar is minimal interruption above all else, this stage of scrutiny could really feel heavier.
The repeated G2 themes and a powerful 4.5/5 ranking on G2 level to Okta as a reliable id core for zero belief: simple SSO, robust MFA, and broad integrations that make safe entry really feel routine. In the event you make investments a little bit of time in console orientation and tune MFA/session insurance policies to match your danger mannequin, you get the payoff most reviewers describe — fewer credentials to handle, clearer entry paths, and a cleaner handoff between safety and productiveness.
What I like about Okta:
- Friction-light SSO with a well-recognized app portal that customers undertake rapidly. G2 reviewers repeatedly credit score this with fewer “the place do I log in?” tickets and smoother day-to-day entry.
- It has a broad ecosystem match: deep integrations with SaaS/legacy apps plus HRIS, EDR/MDM, SIEM, and ticketing, so onboarding/offboarding and incident handoffs really feel predictable.
What G2 customers like about Okta:
“What I like finest about Okta is how effortlessly it brings the whole lot collectively. As an alternative of juggling a number of logins and passwords, I simply check in as soon as and growth, I’m in. Whether or not its work apps, e-mail, or instruments I take advantage of every day, Okta makes entry really feel seamless and safe. The peace of thoughts understanding that multi-factor authentication is quietly working within the background is a big plus. Its like having a wise gatekeeper who by no means sleeps. Additionally, the interface is clear and intuitive — even for somebody who’s not tremendous tech-savvy. It simply works, and that’s what I admire most. The combination may be very simple as properly.“
– Okta assessment, Mohammed O.
What I dislike about Okta:
- The console prioritizes breadth and granular management, which energy customers will admire, however it might probably really feel busy at first till roles, teams, and workflows are dialed in.
- Stronger MFA and gadget checks increase safety posture, although some groups could discover further prompts till risk-based guidelines and session insurance policies are tuned to their surroundings.
What G2 customers dislike about Okta:
“The principle downside is that the preliminary setup and configuration is usually a bit advanced, particularly for groups with out a lot expertise in id administration. Additionally, the pricing can really feel just a little excessive for smaller firms. Nevertheless, as soon as it’s correctly arrange, the platform works very reliably.”
– Okta assessment, Daniel Alberto J.
3. Zscaler Non-public Entry: Greatest for zero-trust entry to inner apps (no VPN)
Amongst zero belief choices for personal app entry, Zscaler Non-public Entry (ZPA) exhibits up repeatedly in G2 critiques for doing what most groups really want: dealer quick, policy-driven, user-to-app connectivity. In case your aim is to retire brittle VPN tunnels, scale back lateral motion, and provides customers a constant strategy to attain inner internet, client-server, and cloud apps from anyplace, ZPA is constructed for that job.
What G2 customers name out most frequently is how safe entry feels routine as soon as ZPA is in place. In truth, 92% of G2 customers price the appliance safety extremely. The mixture of identity-aware insurance policies and least-privilege entry means you possibly can tighten management whereas retaining the expertise easy, individuals launch the apps they want, and nothing else.
Reviewers additionally spotlight the worldwide footprint and scaling conduct: standing up entry for distributed groups and contractors is easy, and insurance policies can broaden with new apps and areas with out main re-architecture. In day-to-day phrases, that interprets into fewer “can’t attain the app” tickets and fewer time spent micromanaging community paths.
The time-to-value and setup practicality typically comes up as a constructive in G2 critiques. Many admins describe the preliminary rollout as clear. There are publishing apps, mapping insurance policies to id teams, and onboarding customers with minimal to no friction. ZPA’s ecosystem match additionally will get constant reward: integrations with main IdPs for SSO/MFA, plus hooks into EDR/MDM and SIEM/ticketing, assist groups maintain id, gadget posture, and audit alerts in a single loop.
Let’s speak about efficiency. Customers observe snappy entry and low perceived latency in comparison with legacy VPN, particularly for internet apps, with fewer slowdowns as a consequence of tunnel congestion. Coupled with consumer and connector structure that abstracts away community complexity, many groups say ZPA makes distant entry really feel invisible: customers click on, the service verifies id and gadget posture, and the session simply works. For IT, that “looks like SaaS” high quality is a giant a part of why ZPA replaces tactical VPNs relatively than sitting subsequent to them.
A number of G2 reviewers say the agent/consumer wants hands-on tuning within the first couple of weeks (tightening guidelines, mapping app segments, refining device-posture checks). That is finest for groups that need granular, policy-driven management relatively than pure plug-and-play. After insurance policies settle, VPN tickets drop, entry is predictable and quick, and safety has clear visibility into who accessed what, from which gadget, underneath which situations.
G2 finances homeowners observe that pricing scales with footprint (areas + app-dense estates), so that you’ll want progress modeling up entrance. Appropriate for organizations planning international protection and broad integrations; much less splendid in case you anticipate flat, set-and-forget pricing. With early modeling, spend turns into predictable, consolidation offsets prices so groups see sturdy beneficial properties, much less lateral motion, fewer brittle tunnels — and a person expertise the place individuals don’t battle.
A modest upfront funding in consumer/coverage tuning and scale modeling yields what groups worth most: quick, predictable private-app entry, fewer VPN tickets, and clear end-to-end visibility. In observe, ZPA scales with your small business and largely will get out of the best way—tightening management with out including friction.
What I like about Zscaler Non-public Entry:
- Safe entry feels routine: identity-aware, least-privilege user-to-app connectivity and lowering “can’t attain the app” tickets.
- Robust ecosystem match and rollout: clear IdP/SSO/MFA integration plus hooks into EDR/MDM and SIEM/ticketing; admins repeatedly observe a transparent, methodical preliminary setup and predictable day-two ops.
What G2 customers like about Zscaler Non-public Entry:
“What I like most about Zscaler Non-public Entry is that it fully removes the effort of utilizing a standard VPN. As soon as it’s arrange, customers can securely entry inner apps from anyplace with out worrying about connecting to the company community. The zero-trust strategy feels a lot safer as a result of entry is given solely to what’s wanted. It additionally integrates properly with id suppliers like Okta or Azure AD, which makes person administration easy. Yet one more benefit is that it notices each Ethernet connection.”
– Zscaler Non-public Entry assessment, Rushi P.
What I dislike about Zscaler Non-public Entry:
- The consumer and coverage mannequin prioritize granular management and steady checks, which is nice for safety posture, however the first weeks could contain tuning app segments and posture guidelines to attenuate prompts.
- Enterprise-grade protection and international scale are strengths, although pricing/licensing can profit from upfront modeling as app inventories and areas broaden, particularly in massive, app-dense environments.
What G2 customers dislike about Zscaler Non-public Entry:
“At occasions, the preliminary configuration and coverage setup is usually a bit advanced, particularly for brand new directors. The troubleshooting course of when customers face entry points is also extra intuitive, as logs and diagnostics generally require deeper technical experience. Moreover, occasional latency can happen when connecting to functions hosted in sure areas. Nevertheless, as soon as correctly configured, it performs very reliably and requires minimal upkeep.”
– Zscaler Non-public Entry assessment, Pratik Ok.
4. ThreatLocker: Greatest for endpoint least-privilege and allowlisting
Amongst endpoint controls constructed for a default-deny posture, ThreatLocker exhibits up repeatedly in G2 critiques for doing the blocking-and-tackling that really shrinks the assault floor. These embody utility allowlisting/whitelisting, community and storage management, and guardrails that cease unknown executables earlier than they run.
It’s a powerful match for safety groups that need granular, policy-driven management on Home windows/macOS/Linux endpoints—particularly MSPs and lean IT teams that must implement least privilege with out standing up a full EDR engineering perform.
What stood out in my analysis — and echoed throughout G2 critiques — is how rapidly you possibly can transfer from permissive to default-deny with out paralyzing customers. Reviewers repeatedly name out utility management because the anchor: construct a clear stock of what’s allowed, then let ThreatLocker deal with the remainder. In observe, meaning fewer “thriller binaries” and much much less room for ransomware and script-based abuse. Paired with Ringfencing® to constrain what an allowed app can contact (e.g., which processes it might probably spawn, what it might probably learn/write), groups describe a significant drop in dangerous behaviors with out breaking legit workflows.
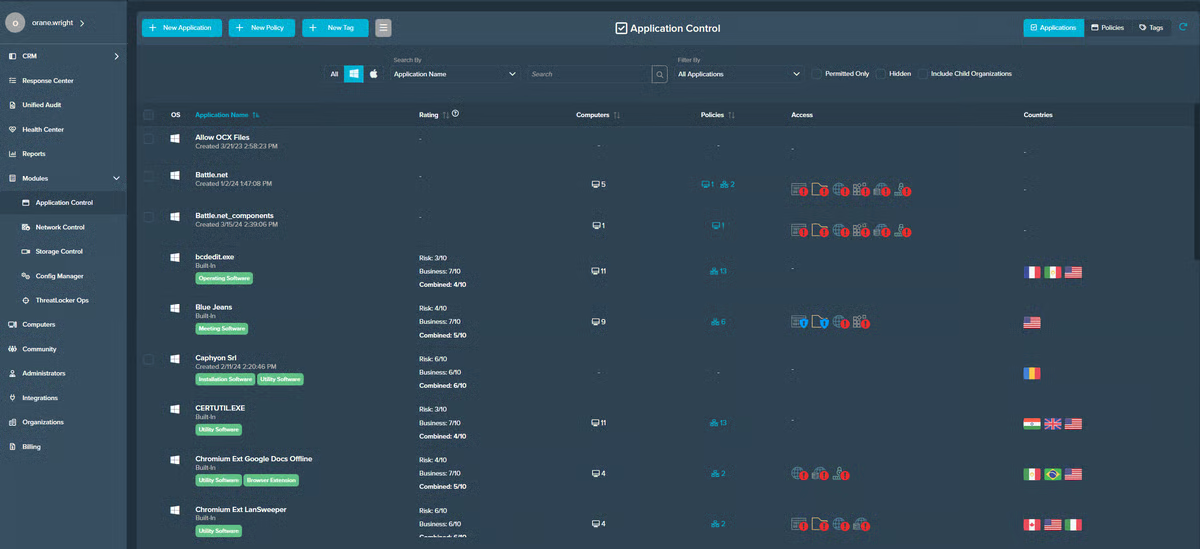
G2 customers additionally spotlight the breadth of coverage controls past functions: Community Management to limit outbound/inbound communications, and Storage Management to control USB/exterior media use. That layered strategy exhibits up in suggestions as tangible outcomes — blocking lateral motion paths, stopping knowledge exfil over unauthorized channels, and eliminating “USB roulette” with out countless guide policing. The online impact is that on a regular basis endpoint exercise turns into predictable and explainable, which simplifies audits and incident timelines.
One other recurring theme is time-to-value. Many reviewers describe easy deployment and onboarding that get you to an enforceable posture rapidly, with intuitive administration as soon as insurance policies settle. The admin interface and coverage views are often credited for making a posh management mannequin legible—groups can see what was blocked, why, and what rule adjusted the result.
Simply as importantly, G2 customers constantly reward assist: quick responses, hands-on steering throughout rollout, and collaborative tuning when approvals spike or an edge case seems. That “assist if you want it” loop is a giant a part of why ThreatLocker lands properly with MSPs and resource-constrained IT groups.
G2 reviewers constantly name out the depth and precision the platform brings to entry management, with many noting that the primary few weeks are finest spent refining approvals, fine-tuning coverage teams, and aligning workflows, notably in multi-site or mixed-OS environments. As a result of the agent and UI are designed for optimum management and visibility, groups anticipating a purely plug-and-play expertise typically make investments just a little time in coaching and coverage design up entrance. As soon as baselines are tuned, approvals normalize, and the platform largely fades into the background, lowering noise whereas delivering extra predictable and safe entry.
The default-deny posture is a deliberate design alternative, and G2 suggestions suggests it might probably floor extra prompts early in a deployment. Groups that stage their rollout, talk expectations clearly, and tighten Ringfencing®, Community, and Storage insurance policies report that the sign stabilizes quickly. As insurance policies mature, approvals drop to a manageable rhythm, and customers profit from a safe, predictable expertise, one which raises the safety bar with out creating new friction.
General, rated a excessive 4.8/5 on G2, ThreatLocker stands out for much less noise, fewer blind spots, and much fewer “why did this run?” tickets.
What I like about ThreatLocker:
- Default-deny with allowlisting + Ringfencing makes endpoint conduct predictable. I can present precisely what ran, what it was allowed to the touch, and why a block occurred.
- Layered Community/Storage Management closes widespread abuse paths (unauthorized outbound visitors, USB misuse) with out countless guide policing, which G2 customers say simplifies audits and day-to-day ops.
What G2 customers like about ThreatLocker:
“ThreatLocker is a strong safety answer that provides directors full management over what customers can set up, run, or script. Its default-deny strategy ensures that solely explicitly accepted actions are allowed, making it simple to sleep at night time understanding that even when customers click on on harmful information, they received’t execute in safe mode.”
– ThreatLocker assessment, Graham T.
What I dislike about ThreatLocker:
- The console’s precision rewards groups that put money into early coverage hygiene, anticipate a brief part of tuning approvals and refining teams earlier than noise settles.
- In order for you pure plug-and-play, plan a little bit of enablement/coaching; most reviewers observe worth unlocks quickest when admins study the workflow for edge-case approvals in multi-site or mixed-OS estates.
What G2 customers dislike about ThreatLocker:
“ThreatLocker is a posh software that provides many options with granular management. For that motive it does include a big studying curve. It’s extremely beneficial that you just work intently with their assist group till you’re fully comfy with the ins and outs of the software program.”
– ThreatLocker assessment, Bryan S.
5. Cato SASE Cloud: Greatest for unified community + safety at international scale
Amongst platforms constructed to converge networking and safety within the cloud, Cato SASE Cloud exhibits up repeatedly in G2 critiques for making distributed connectivity really feel less complicated and extra predictable. It’s designed for groups that wish to collapse SD-WAN, safe internet gateway, CASB, FWaaS, and ZTNA right into a single service operating on a world spine, so customers get constant efficiency and safety whether or not they’re in a department, at dwelling, or on the transfer.
In case your aim is to switch a patchwork of home equipment and level instruments with one coverage aircraft and one consumer, that is the sort of platform G2 customers maintain shortlisting.
Within the suggestions I reviewed, the primary throughline is efficiency consistency. G2 customers often observe that Cato’s international non-public spine and dense PoP presence clean out latency spikes and Web variability, particularly for SaaS and real-time visitors. The only, cloud-delivered console centralizes community and safety coverage, dwell visitors analytics, and incident views, which reviewers say reduces swivel-chairing and speeds troubleshooting. For a lot of organizations, that mixture turns day-two operations right into a quicker, extra routine movement.
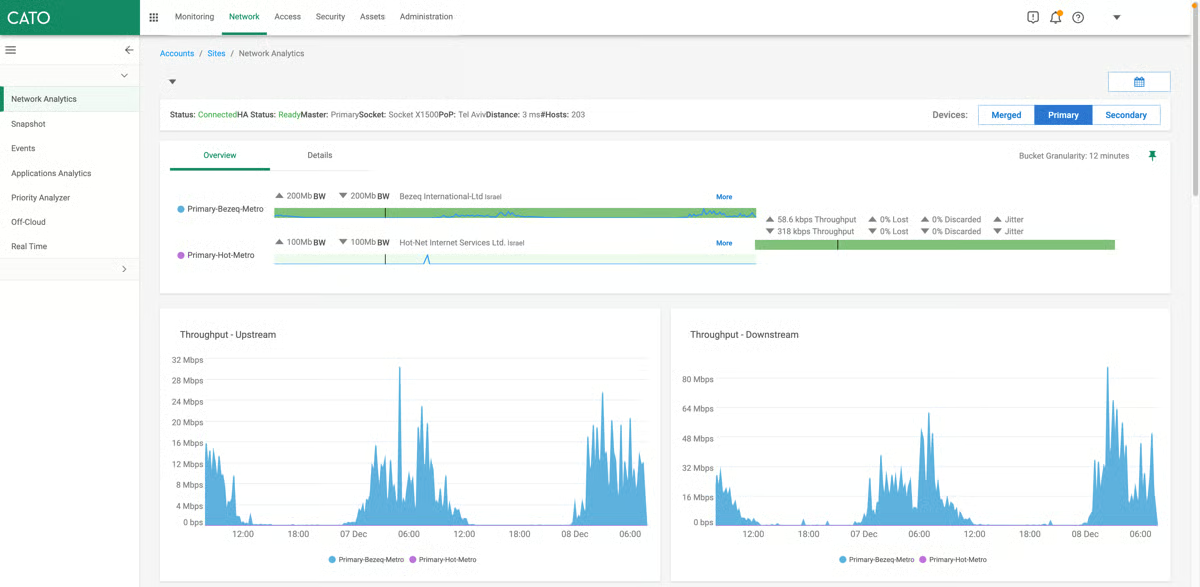
A second theme is convergence with out contortions. G2 critiques constantly name out how SD-WAN and safety controls dwell facet by facet: app-aware routing, QoS, and hyperlink remediation run alongside SWG/CASB, ZTNA, and firewalling, so that you don’t must daisy-chain distributors or hairpin visitors by way of a central hub. Admins spotlight the sensible results: fewer VPN tickets, cleaner least-privilege entry to personal apps, and coverage reuse throughout areas and customers.
When it’s time to carry a brand new web site on-line, reviewers say deployment is methodical and fast: ship an edge gadget, register it, connect insurance policies, and also you’re on the spine with safety controls already in line. 93% of G2 critiques price the community segmentation extremely, guaranteeing administrative management over community parts, mapping, and segmentation.
G2 customers additionally emphasize visibility and management. The platform’s real-time analytics and historic reporting make it easy to see who accessed what, from the place, and underneath which coverage, which helps each with incident timelines and with routine capability planning.
Many reviewers level to MDR choices and proactive assist as drive multipliers: when one thing drifts, you hear about it with actionable steering relatively than discovering it throughout an outage window. That assist expertise exhibits up typically in feedback about smoother rollouts and shorter time-to-value.
G2 reviewers admire the unified mannequin, however groups coming from appliance-heavy networks typically spend the primary weeks mapping legacy guidelines to cloud insurance policies and tuning ZTNA app definitions so prompts and paths mirror actual utilization. Reviewers body this as an onboarding actuality, not a blocker, and observe that when insurance policies settle, tickets drop and routing/safety really feel predictable.
Pricing scales with footprint. As you add areas, websites, and app protection, whole spend grows, so budgets want upfront modeling to keep away from surprises, in accordance with G2 finances homeowners. This mannequin fits organizations pursuing international protection and power consolidation (SD-WAN + safety + ZTNA in a single service) who worth paying in proportion to utilization. Nevertheless, it’s much less splendid in case you anticipate flat, set-and-forget pricing no matter progress. Groups that mannequin progress early say spend turns into predictable, consolidation trims vendor sprawl and assist contracts, and the operational upside holds, fewer brittle tunnels, constant inspection, and a single coverage aircraft because the community expands.
G2 suggestions describes regular payoff: branches and distant customers journey the identical spine with constant inspection, ZTNA replaces brittle tunnels, and admins function from a single coverage aircraft that travels with customers and apps.
What I like about Cato SASE Cloud:
- The worldwide non-public spine + dense PoPs smooths real-world latency and makes SaaS/real-time visitors really feel constant.
- True convergence: SD-WAN lives alongside SWG/CASB, FWaaS, and ZTNA, so websites come on-line methodically (ship, register, connect insurance policies) and you’ll reuse insurance policies throughout customers/areas.
What G2 customers like about Cato SASE Cloud:
“What I like finest about Cato SASE Cloud is the centralized, all-in-one platform that seamlessly combines SD‑WAN, firewall, SWG, CASB, and ZTNA providers underneath a single pane of glass. Deployment and onboarding are quick—spinning up new websites takes underneath an hour — and day-to-day administration is way less complicated in comparison with juggling a number of instruments, separate interfaces, and licenses.”
– Cato SASE Cloud assessment, Mohan S.
What I dislike about Cato SASE Cloud:
- Coming from an appliance-heavy previous, you’ll doubtless map legacy guidelines to cloud insurance policies and tune ZTNA app definitions within the first weeks; groups say this upfront work pays off as tickets drop and paths develop into predictable.
- Pricing is finest modeled upfront, particularly for a lot of small websites or app-dense estates, however consolidation (spine + SD-WAN + safety stack) can offset the associated fee and simplify vendor sprawl.
What G2 customers dislike about Cato SASE Cloud:
“What I dislike about Cato SASE Cloud is that superior customization and granular management choices are considerably restricted in comparison with conventional firewalls. Reporting and analytics could possibly be extra detailed and versatile, and coverage updates generally take a couple of minutes to use. Whereas the platform is steady and bettering, it is nonetheless maturing in some enterprise-level options.”
– Cato SASE Cloud assessment, Faiz P.
Greatest zero belief networking software program: Incessantly requested questions (FAQs)
Bought extra questions? G2 has the solutions!
Q1. What’s one of the best zero belief platform for cloud providers?
For cloud-first entry, pair Okta for identity-driven SSO/MFA and conditional entry with Zscaler Non-public Entry (ZPA) for user-to-app connectivity with out VPNs. If workplaces/branches want constant efficiency too, Cato SASE Cloud provides a world spine with inline safety so cloud apps keep quick and ruled finish to finish.
Q2. What are the highest zero belief community options for small enterprise?
Lean groups usually get fast wins with ZPA (easy, policy-driven entry to inner apps) anchored by Okta (simple SSO/MFA and app assignments). In the event you additionally need one console for connectivity + safety as you develop, Cato SASE Cloud consolidates SD-WAN and safety controls with out equipment sprawl.
Q3. What are one of the best zero belief suppliers for enterprise cybersecurity?
Enterprises typically mix Okta (listing/SSO/MFA + lifecycle) with Cato SASE Cloud (international SD-WAN + SWG/CASB/ZTNA). For vegetation, labs, or sensible buildings, Palo Alto Networks IoT/OT Safety provides gadget discovery, danger scoring, and segmentation.
This fall. What are some zero belief networking app suggestions?
For inner apps, ZPA brokers direct user-to-app entry primarily based on id and gadget posture. Maintain permissions clear in Okta (teams, conditional entry), and harden endpoints with ThreatLocker (allowlisting + ringfencing) so accepted apps can solely do what they need to.
Q5. Which zero belief product ought to we use for community security?
If “community security” means chopping lateral motion and stopping dangerous executables, ThreatLocker provides you a default-deny on endpoints, whereas ZPA removes broad community publicity by going app-by-app. Use Okta to centralize authentication so entry stays tied to the person and gadget context.
Q6. What’s the most dependable zero belief service for our tech startup?
Startups often need quick rollout and minimal overhead: Okta for fast SSO/MFA and clear onboarding/offboarding, plus ZPA to publish inner instruments with out standing up VPNs. In the event you’re opening workplaces or want WAN + safety in a single place, Cato SASE Cloud retains it easy as you scale.
Q7. What are the main zero belief software program for shielding enterprise knowledge?
Shield knowledge by aligning id, entry, and endpoints: Okta applies conditional entry, ZPA ensures least-privilege paths to delicate apps, and ThreatLocker prevents unapproved binaries or scripts from touching protected information. For site-to-site visitors, Cato SASE Cloud enforces coverage in all places.
Q8. What’s a trusted zero belief supplier for SaaS firms?
SaaS-heavy groups do properly with Okta (centralized SSO/MFA and app governance) plus ZPA (safe entry to personal construct instruments, admin panels, and databases). In the event you function globally, Cato SASE Cloud provides a constant safety layer and efficiency baseline for SaaS and personal apps alike.
Q9. What’s a zero belief answer for securing an workplace community?
If workplaces/branches are in scope, Cato SASE Cloud converges SD-WAN and safety (SWG/CASB/ZTNA) on a cloud spine, so coverage is constant in all places. Use Okta to gate entry and ZPA to achieve inner apps securely; for services with related units, add Palo Alto Networks IoT/OT Safety to find and phase IoT/OT.
Able to retire your VPN?
Constructing sturdy entry management shouldn’t imply wrestling with clunky purchasers or brittle community tunnels. The 5 instruments I examined make it simpler to ship safe, personalised entry, whether or not you’re centered on retiring VPNs, segmenting delicate apps, or enabling contractors and BYOD safely.
Every decide is a extremely beneficial choice for lowering the assault floor and stabilizing the person expertise. Some shine for quick, light-weight rollouts; others go deeper with analytics and segmentation as you scale. I highlighted what every does properly, and the place to observe for limits, so you possibly can transfer quicker towards a zero belief posture that really holds up.
Now it’s your flip: examine your prime two or three, map them to your stack and danger areas, and select the platform that retains customers transferring whereas retaining threats contained.
Able to layer adaptive challenges on prime of ZTNA? Discover the finest risk-based authentication software program to pair zero belief entry with step-up MFA primarily based on person and gadget danger.

